Introduction
After successfully integrating Keycloak with Rancher Server to centrally manage authentication and authorization for Kubernetes clusters, I explored an approach to integrate Microsoft Entra ID(formerly Azure AD) to further enhance identity management.
In this article, we will go through the necessary steps to enable Microsoft Entra ID users to access Kubernetes clusters via Rancher Server, ensuring seamless authentication and fine-grained RBAC.
What is Microsoft Entra ID?
Microsoft Entra ID(formerly known as Azure Active Directory) is a cloud-based identity and access management service used by organizations to manage user authentication and secure access to applications, services, and resources.
Architecture Overview
The overall architecture of this setup is shown below:
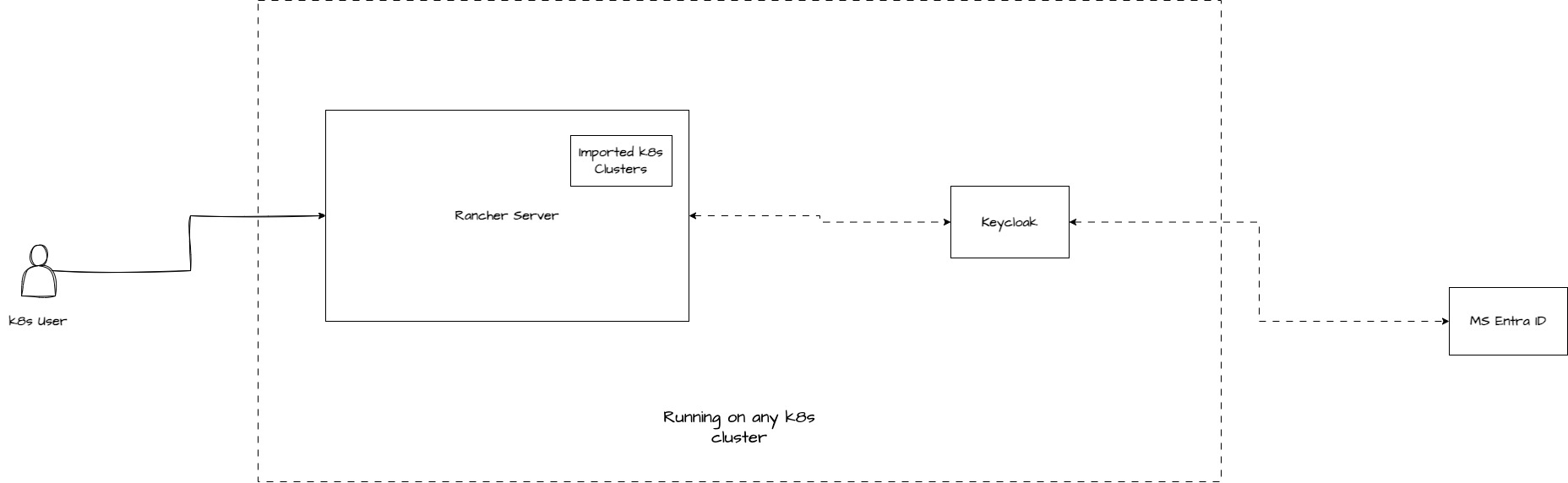
We will not cover the basic installation of Rancher Server and Keycloak in this guide, as there are many readily available resources for that. Instead, we will focus on integrating Microsoft Entra ID with Keycloak and Rancher Server, enabling MS Entra ID users to access Kubernetes clusters while enforcing fine-grained access controls.
Steps Overview
Here’s a high-level breakdown of the integration process:
- Configure an application in Microsoft Entra ID for our use case.
- Integrate Microsoft Entra ID with Keycloak to enable federated authentication.
- Integrate Keycloak with Rancher Server for identity propagation.
- Import/Create Kubernetes clusters in Rancher Server.
- Configure RBAC policies in Rancher Server to control access to Kubernetes clusters.
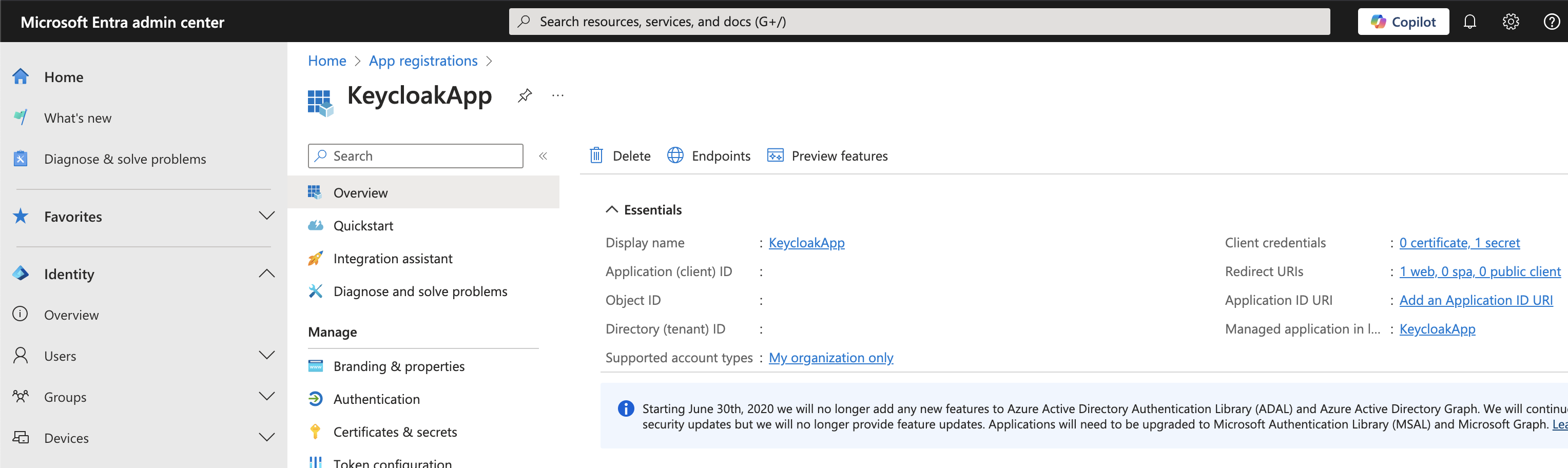
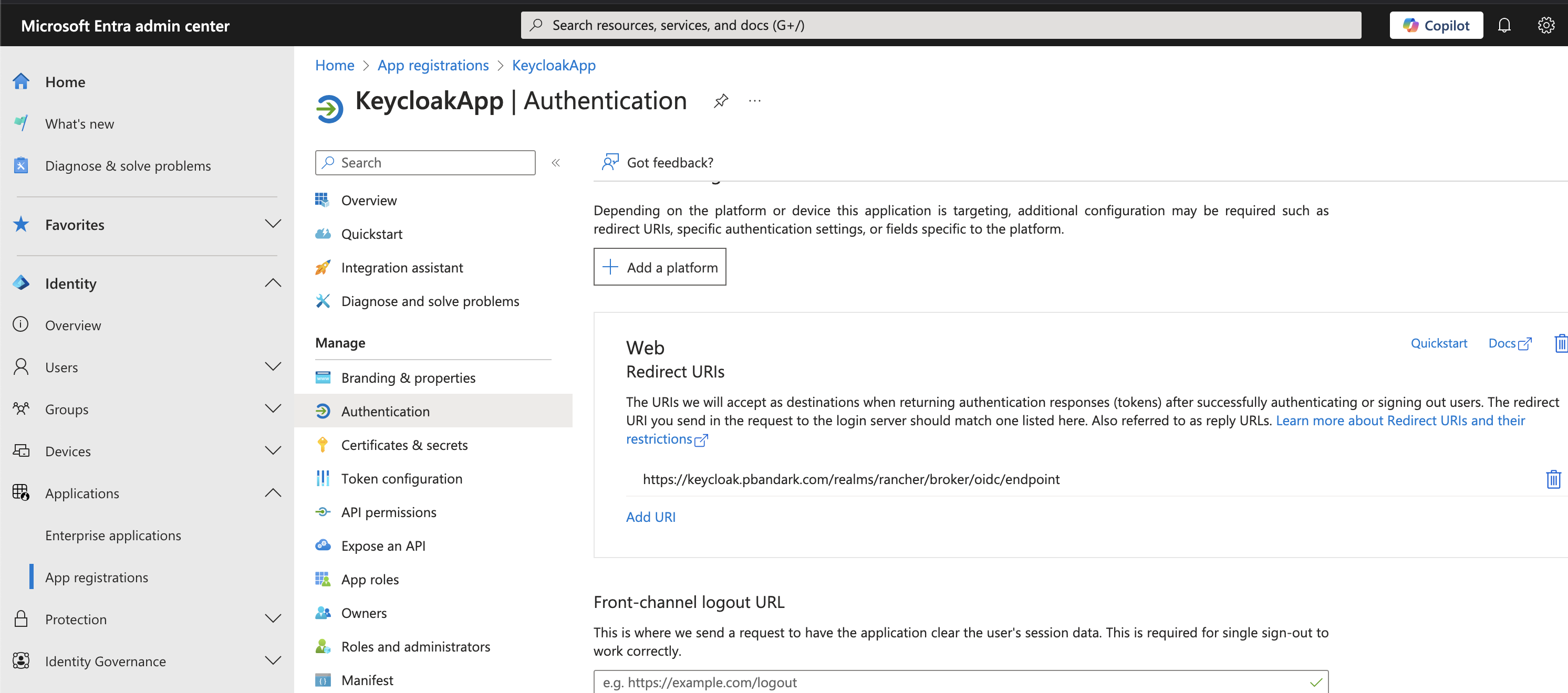
Step 1: Configure an Application in Microsoft Entra ID
To allow authentication through Microsoft Entra ID, we need to register an application and configure it appropriately.
You can refer below screenshots from my lab setup to configure an application in MS Entra ID:
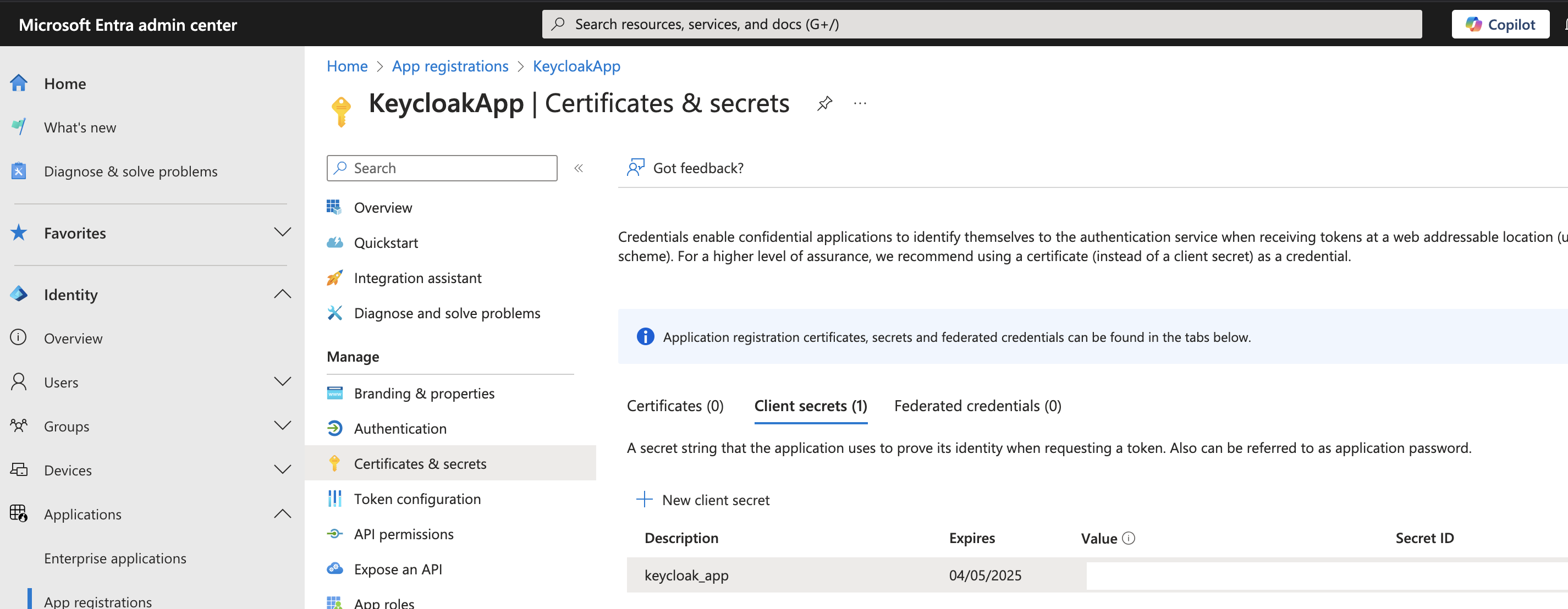
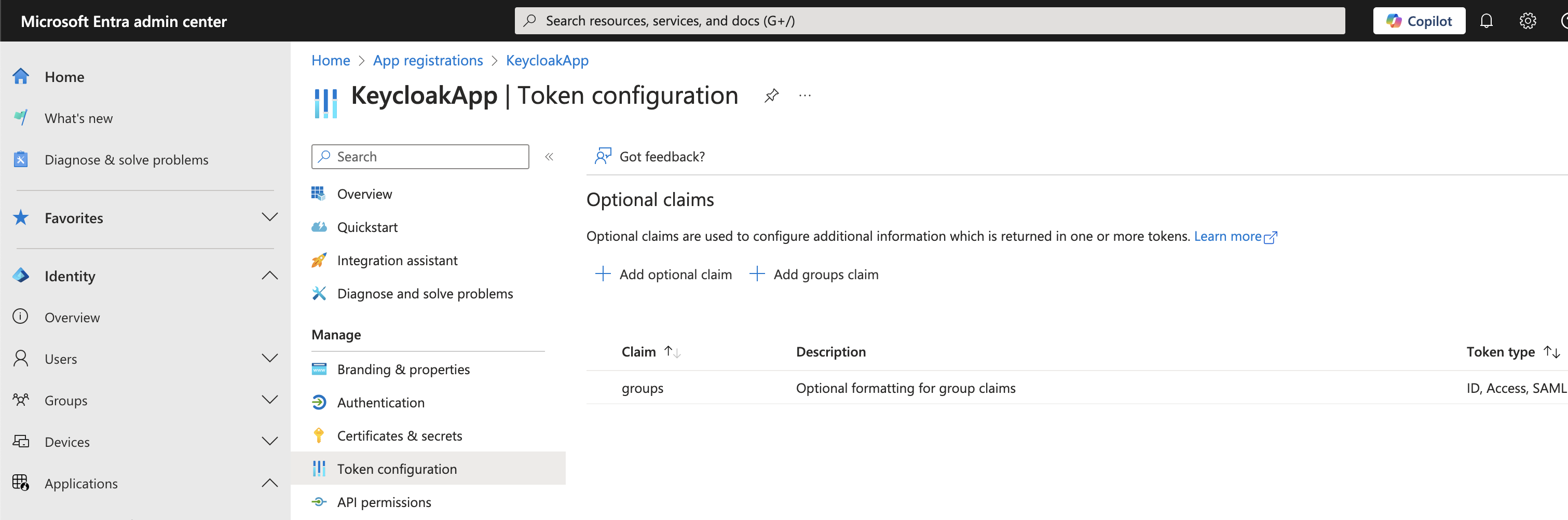
Step 2: Integrate Microsoft Entra ID with Keycloak
Once the application is set up in MS Entra ID, we need to integrate it with Keycloak, allowing Keycloak to use Entra ID as an external identity provider.
You can refer these screenshots from my lab setup to configure Keycloak:
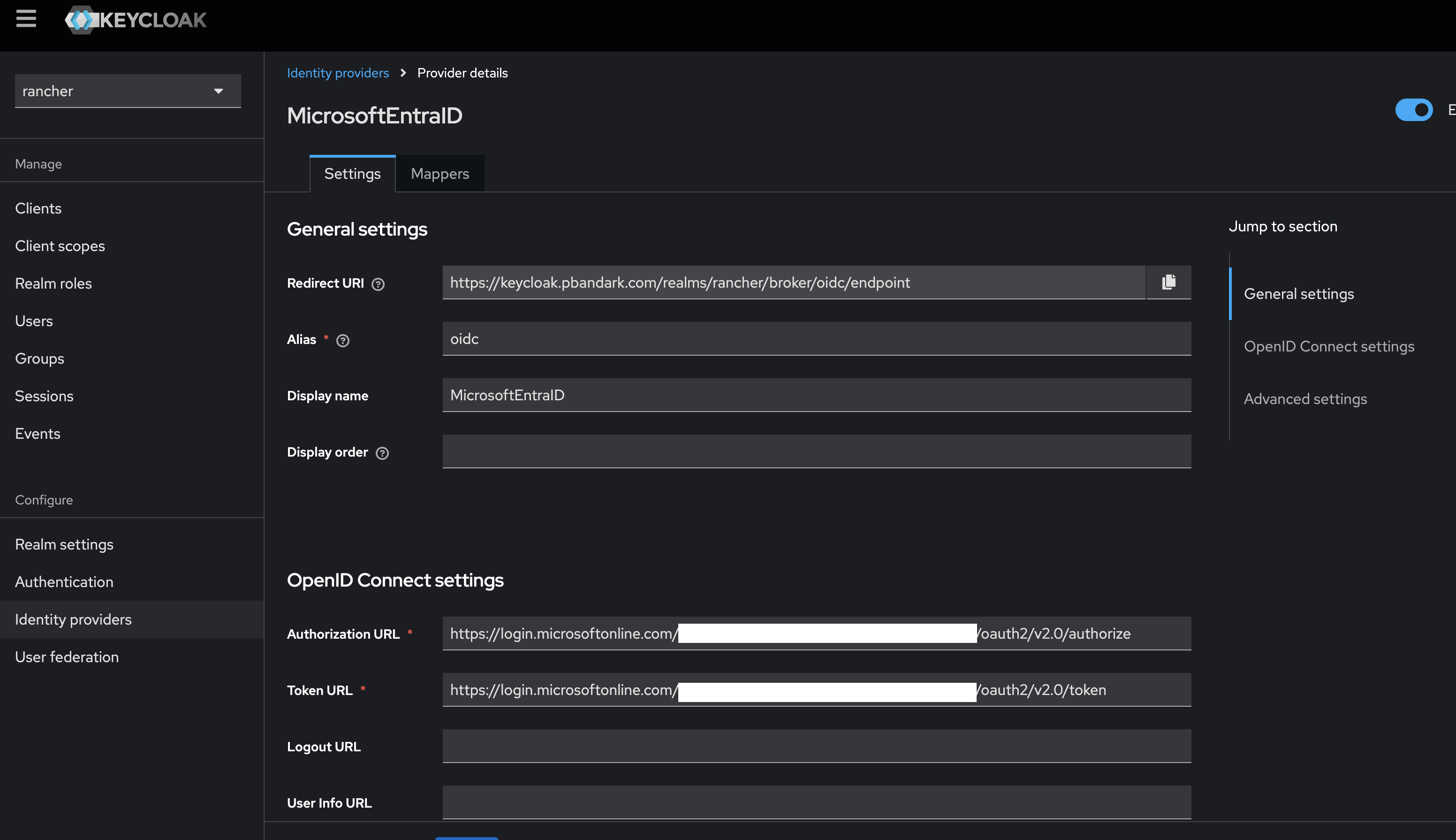
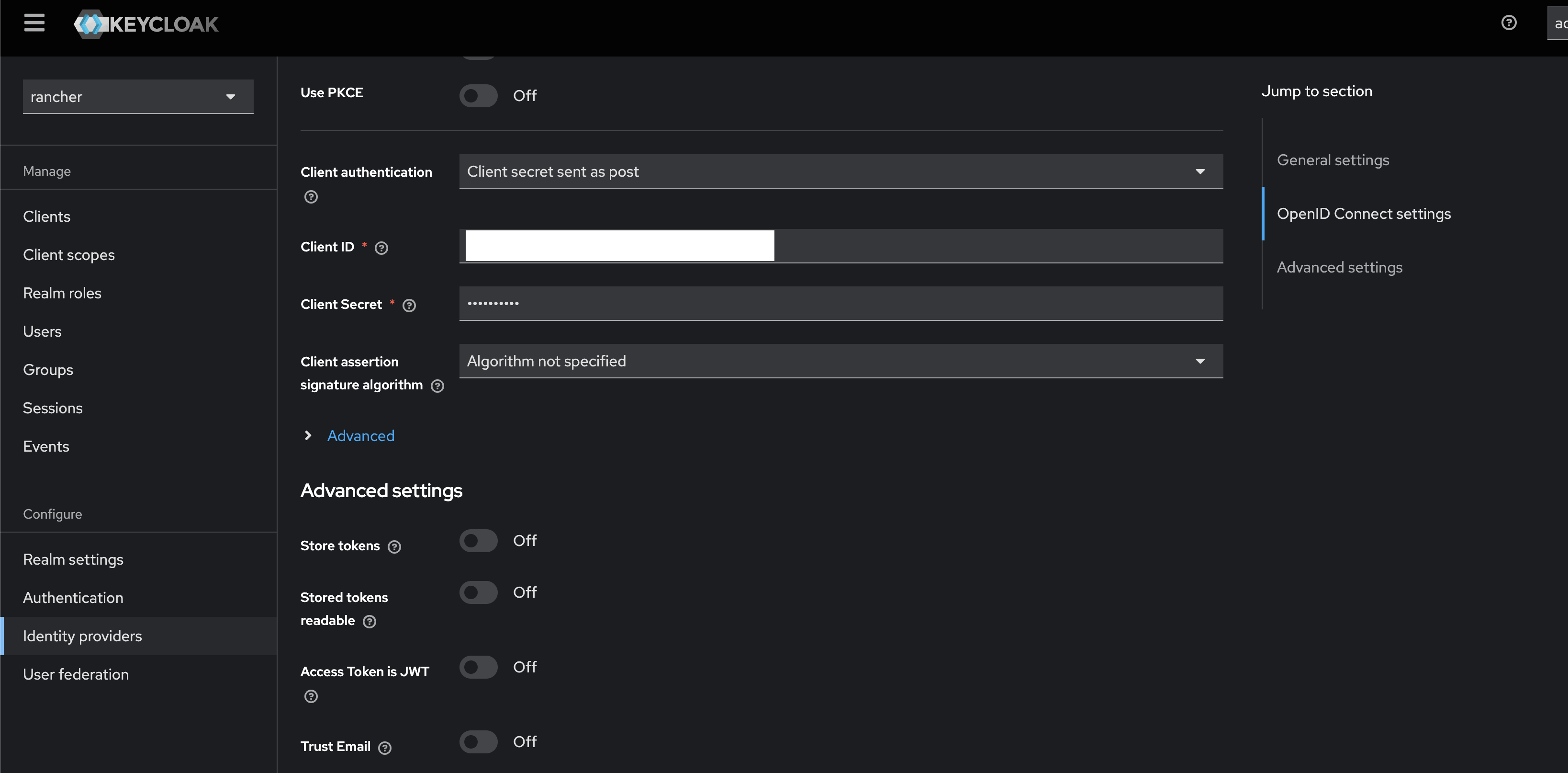
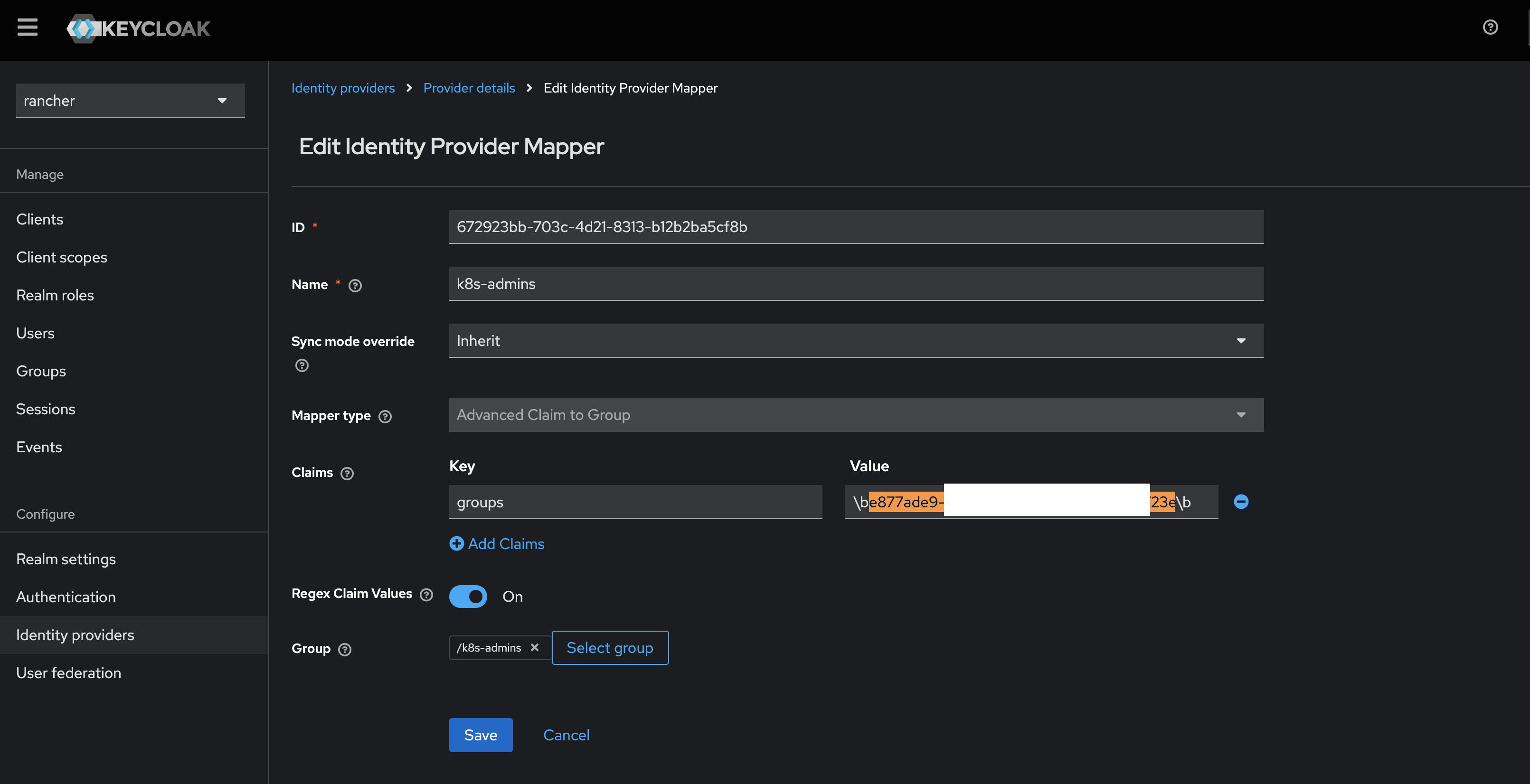
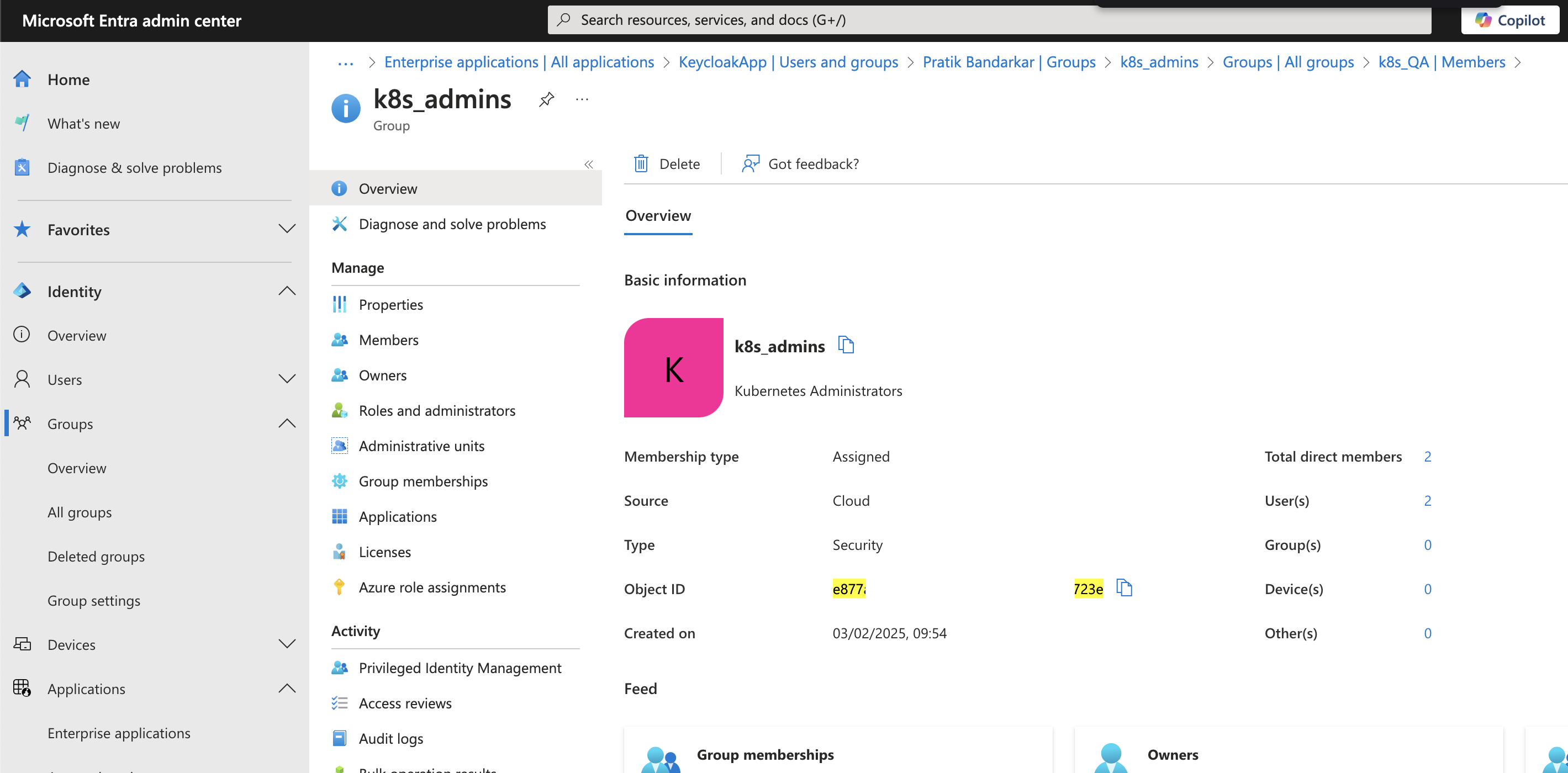
Step 3: Integrate Keycloak with Rancher Server
Now that MS Entra ID is integrated with Keycloak, the next step is to integrate Keycloak with Rancher Server, allowing Rancher to authenticate users via Keycloak.
You can refer to my previous blog on integrating Keycloak with Rancher.
Step 4: Import or Create Kubernetes Clusters in Rancher
Once authentication is in place, we need to import or create Kubernetes clusters in Rancher Server to manage access centrally.
This can be done via Rancher Server UI, where you can either:
- Import an existing Kubernetes cluster.
- Create a new cluster using Rancher’s built-in provisioning options.
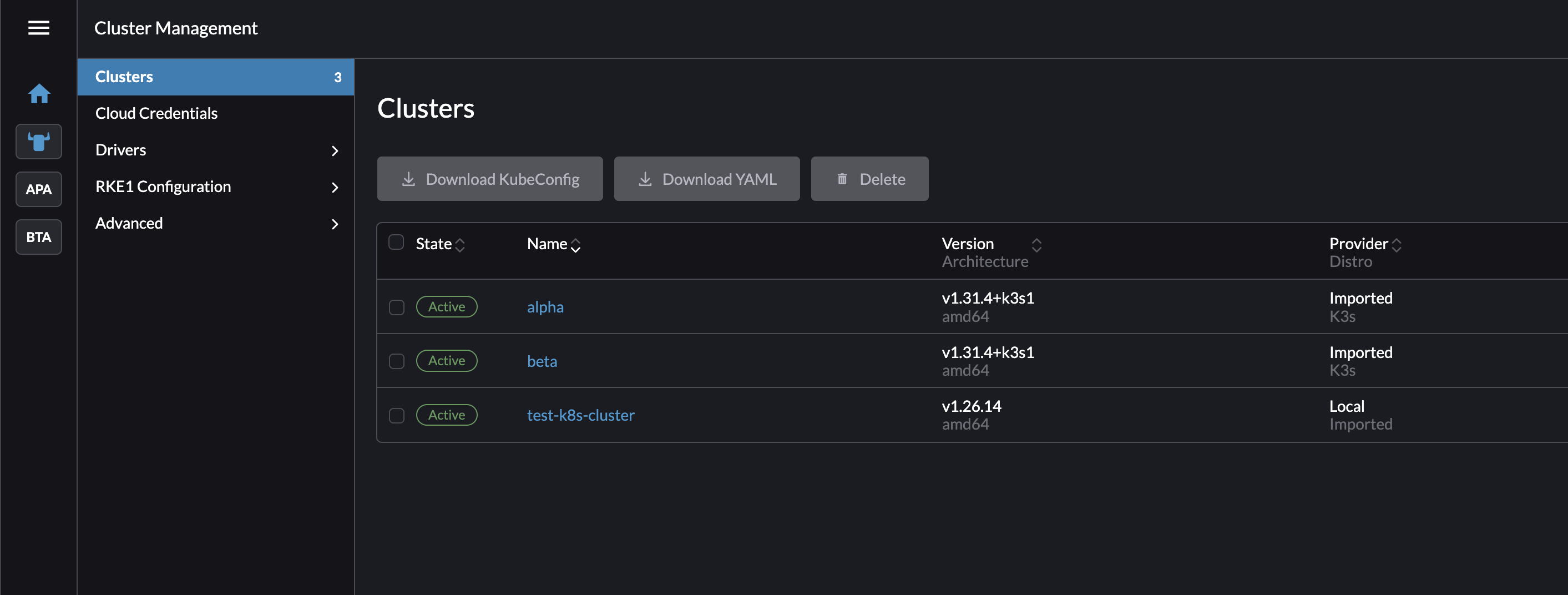
Step 5: Configure RBAC to Allow Kubernetes Access from Rancher
With all integrations in place, the final step is to configure RBAC policies in Rancher Server to control access to the Kubernetes clusters based on Microsoft Entra ID groups.
Since Keycloak is now receiving group information from Entra ID, we can map those groups to roles in Rancher.
You can refer to my previous blog on RBAC configuration in Rancher.
Validation: Testing the Setup
To verify that everything is working as expected, we’ll test access using a user from Microsoft Entra ID.
For this test, we are using the Hayden user from MS Entra ID, who belongs to the k8s_dev_users group.
- The
k8s_dev_usersgroup is mapped to theDevgroup in Keycloak. - The
Devgroup hasread-only accessto thetrinitynamespace in thealphaKubernetes cluster(configured in step 5 above).
- Attempting to list nodes(denied):
[root@bastion]# kubectl get node
Error from server (Forbidden): nodes is forbidden: User "u-odsw5u5ejw" cannot list resource "nodes" in API group "" at the cluster scope- Listing pods in the “trinity” namespace(allowed):
[root@bastion]# kubectl get pod -n trinity
NAME READY STATUS RESTARTS AGE
nginx-676b6c5bbc-szwxb 1/1 Running 0 18d- Attempting to list pods in the “default” namespace(denied):
[root@bastion]# kubectl get pod -n default
Error from server (Forbidden): pods is forbidden: User "u-odsw5u5ejw" cannot list resource "pods" in API group "" in the namespace "default"The test confirms that the RBAC policies were successfully applied – the user can only view resources in the trinity namespace and is restricted from accessing other namespaces or cluster-wide resources.
Conclusion
By integrating Microsoft Entra ID with Keycloak and Rancher Server, we can extend enterprise-grade identity management to Kubernetes clusters. This setup enables:
- Seamless authentication using Microsoft Entra ID.
- Centralized user and group management via Keycloak.
- Granular access control through Rancher Server
This approach simplifies multi-cluster access management, enhances security, and ensures that user permissions are consistent across Kubernetes clusters.
I am still exploring further use cases and possibilities. If I discover anything interesting, I will make another blog post. Stay tuned! 😊